Every computer should have a decent anti-virus or security software program installed and hackers know this, which is why unscrupulous computer programmers have marked it out as a lucrative business and one which they can exploit for their own gain. Generally speaking there are three ways they can do this. Let’s take a look at what they are:
One: by profiting from the sale of rogue security software that simply doesn’t work.
Two: by selling fake security software that contains malware that has been programmed to steal your personal data so they can commit identity theft or plunder your bank account, System Doctor 2014 is a great example.
Three: by selling rogue security software that contains malware that has been programmed to steal your personal data so they can sell your personal details, bank account information or credit card numbers on to a third party.
It’s a win win situation for these cyber criminals as they are not only getting paid for an ineffective program which took them little or no effort to create but many of them are stealing your personal information too.
And if you are a victim not only are you paying for a useless program and leaving yourself vulnerable to bank account fraud or identity theft, but the malware can also do serious damage to your computer’s operating system by infecting it with a virus which can lock down your system, destroy your web connectivity or corrupt your files. Not to mention that it display very annoying security center alerts claiming that your computer is infected.
So how does this fake antivirus program work? Firstly, the malware will be called something that is very similar to genuine security software in an attempt to get you to download it. This of course is an obvious ploy but how many of us know all the names of real security software brands anyway? System Doctor 2014 credible sounding, right? Wrong: it's a rogue security application.
The cyber criminals are clever marketers too and will further attempt to fool you and entice you in to buying their program by offering you ‘free’ or ‘trial’ versions of the software or by advertising ‘free upgrades’.
They may also target you with fake pop-up windows that warn you that your computer is infected with a virus or is running slowly because you have unnecessary files stored on your hard drive – and they’ll tell you that by clicking on the window you’ll be able to clean your computer.
Another sneaky way of attempting to get you to download their fake security software is by manipulating search engine results pages so that their own infected website appears as the top result. The majority of us click on the first search result so for a rogue malware programmer this is highly effective. Once you click on the link you’ll be redirected to a home page which will tell you that your computer has a virus – oh but help is as hand because they just so happen to have a free trial for their (rogue!) security software right there.
Another thing to look out for is spam email from so-called software security companies who will send you the bargain of a lifetime – if you just click on the link that they’ve sent you.
So apart from being alert, how else do you protect yourself and make sure you don’t become a victim of one of these scams? Firstly having a genuine security software or anti-virus program installed on your computer is an absolute must. If you’re not sure which names to look out for and are now paranoid about being duped speak to a friend who knows a little more about computers, ask in your local PC store or read online PC magazines to get an idea of what to look for. However it’s not enough just to have security software installed; you also need to make sure that it is up to date and has the latest patches.
Put simply, if you have an outdated anti-virus or worse you don’t have ANY security software installed – do it right now! If you have encountered this malware, please follow the System Doctor 2014 removal guide below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
System Doctor 2014 removal instructions in Safe Mode with Networking:
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
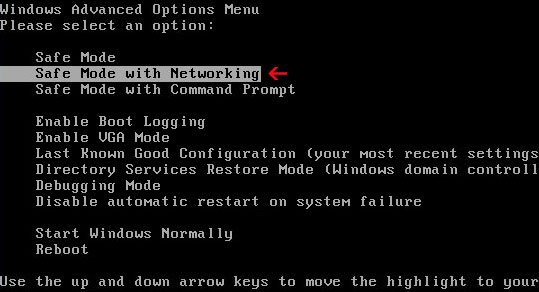
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Open Internet Explorer and download TDSSKiller. Run the utility and click Start Scan to anti-rootkit scan.
3. Then download recommended anti-malware software (direct download) and run a full system scan to remove the rogue program from your computer.
Manual System Doctor 2014 removal instructions:
1. Power off and restart your computer. As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.
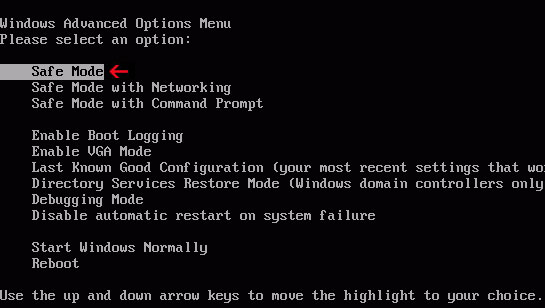
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
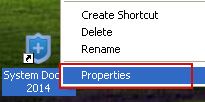
2. Right click on the "System Doctor 2014" icon, click Properties in the drop-down menu, then click the Shortcut tab.
In the Target box there is a path to the malicious file. You can simply click the Target button to open the target folder.
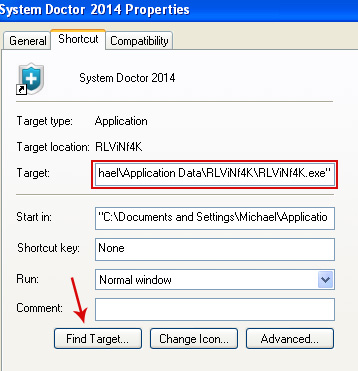
NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmark from the checkbox labeled:
- Hide extensions for known file types
- Hide protected operating system files
Click OK to save the changes. Now you will be able to see all files and folders in the Application Data/Program Data directory.
3. Remove malicious files.
File location, Windows XP:
C:\Documents and Settings\[UserName]\Application Data\[RandomFolder]\[random].exe
File location, Windows Vista/7:
C:\Users\UserName\AppData\Roaming\[RandomFolder]\[random].exe
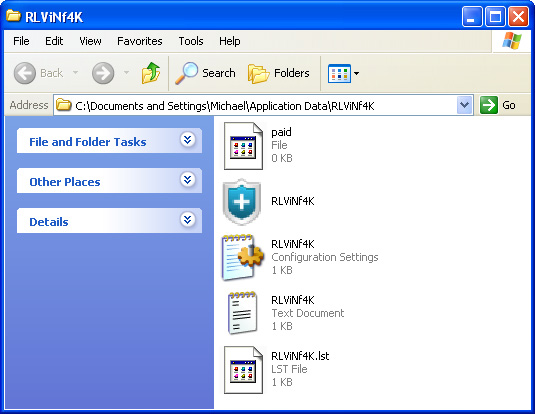
Delete the entire folder or at least the main executable file which in my case was RLViNf4K.
4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.
6. Download recommended anti-malware software (direct download) and run a full system scan to remove System Doctor 2014 virus from your computer.
System Doctor 2014 associated files and registry values:
Files:
- C:\Users\UserName\AppData\Roaming\[RandomFolder]\[random].exe (Win Vista/7)
- C:\Documents and Settings\[UserName]\Application Data\[RandomFolder]\[random].exe (Win XP)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[random]"


















0 comments:
Post a Comment