
Zentom System Guard video:
There are a number of ways that Zentom System Guard gets on your computer, but usually users have no clue as to how they got it. The problem is that rogue security software can appear on your computer without a warning but most of the time cyber crooks use social engineering to trick you into installing their malicious software. For example, this time cyber crooks use fake pop-up window called "System Security Pack Upgrade" that looks just like the legitimate Automatic Windows update screen to trick you into installing Zentom System Guard.
System Security Pack 2010.78.932 (Zentom System Guard Upgrade; KB921472)

Cyber crooks cal also use fake online virus scanners, drive-by-downloads fake codecs and other social engineering tricks. Once installed, Zentom System Guard completes a fake system scan and reports numerous non-existent infections on your computer. Here are some of the fake security alerts you may see when your computer gets infected with Zentom System Guard.

Zentom System Guard - Hacker attack detected
Your computer is subjected to hacker attack. Zentom System Guard has detected that somebody is trying to transfer Your private data via internet. We strongly recommend you to block attack immediately.

Protection Center AlertIf you have accidentally purchased this rogue antivirus program, please contact your credit card company and dispute the charges. The please follow the removal instructions below to remove Zentom System Guard and associated malware from your computer. If you have any questions or need help removing this malware, please leave a comment below. Good luck and be safe online!
To help protect your computer, Zentom System Guard has blocked some features of this program Zentom System Guard has detected unauthorized activity, but unfortunately trial version cannot remove viruses, keyloggers and other treats. Your personal data under serious risk. It is strongly recommended to register Your copy of Zentom System Guard and prevent intrusion for future.
Do You want to block this suspicious software?
Name: Trojan.Win32.Autoit.agg
Alert level: High
Description: It is highly recommended to remove this threat from your PC
Additionally, you can activate the rogue program by entering this registration code MTk4-NzE1-NTYx-NTUw as shown in the image below.

Once this is done, you are free to install anti-malware software and remove the rogue anti-virus program from your computer properly.
Zentom System Guard removal instructions:
1. Download free anti-malware software from the list below and run a full system scan.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
If you can't download it, please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Open Internet Explorer and download STOPzilla. Once finished, go back into Normal Mode and run it. That's It!
Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
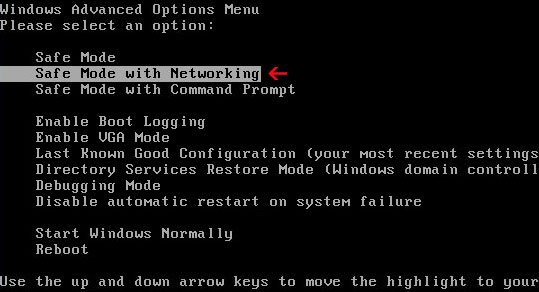
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
Associated Zentom System Guard files and registry values:
Files:

Windows XP
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]\[SET OF RANDOM CHARACTERS].exe
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]\lsrslt.ini
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]\local.ini
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]\hookdll.dll
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]\enemies-names.txt
- C:\Documents and Settings\[UserName]\Start Menu\Programs\Zentom System Guard\
- C:\Documents and Settings\[UserName]\Start Menu\Programs\Startup\Zentom System Guard.lnk
- C:\Documents and Settings\[UserName]\Start Menu\Programs\Zentom System Guard\Uninstall.lnk
- C:\Documents and Settings\[UserName]\Start Menu\Programs\Zentom System Guard\Zentom System Guard.lnk
- C:\Documents and Settings\[UserName]\Desktop\Zentom System Guard.lnk
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]\[SET OF RANDOM CHARACTERS].exe
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]\lsrslt.ini
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]\local.ini
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]\hookdll.dll
- C:\Users\[UserName]\AppData\Roaming\[SET OF RANDOM CHARACTERS]\enemies-names.txt
- C:\Users\[UserName]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zentom System Guard\
- C:\Users\[UserName]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Zentom System Guard.lnk
- C:\Users\[UserName]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zentom System Guard\Uninstall.lnk
- C:\Users\[UserName]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Zentom System Guard\Zentom System Guard.lnk
- C:\Users\[UserName]\Desktop\Zentom System Guard.lnk
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Uninstall\Zentom System Guard
- HKEY_CURRENT_USER\Software\ZentomSystemGuard
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "[SET OF RANDOM CHARACTERS].exe"















0 comments:
Post a Comment