Celas is a new company that represents the world's leading musicians. This company is owned by EMI, GEMA and PRS. If you want to learn more about it, please visit Celas official website. In short, this company stands behind popular artists or right holders and controls over how their music is used. This company is already aware of Celas virus and even made an official statement on this computer locking scam.
Unfortunately, this ransowmare is on the move at the moment. The fake Celas warning hasn't change much since we came across it for the first time, probably in April or May. But it's definitely evolving. Cyber crooks released a new variant which targets U.S. internet users. They also changed payment methods probably because they got banned from payment systems they were using previously.

There are at least five different Celas ransomware warnings that change depending on what part of the continent you are in. The structure and design elements are exactly the same for most countries but of course the wording changes. Anyway, all they trying to do with this is scare you guys to pay for something that you don't need to pay for. If you look at the ransomware you will see that are using pretty strong language. Celas ransomware claims that you were illegally downloading and distributing copyrighted songs.
Some of you guys probably might have fall for it, we know our friends have. But it's all fake. It's just a scam. If they actually caught you doing that they probably won't send you a message asking to pay $100 or euro100 to unlock your PC. That just doesn't make sense at all.
Now, if you're facing an American version of Celas ransomware, you probably noticed that there's only one way to pay the 'fine' – using Ultimate Game Card. That doesn't make sense either. You can use Ultimate Game Card to buy online games and there’s nothing wrong with this service but no one uses this service to actually pay fines. We don't know what were the main reasons why cyber criminals decided to use this service, but it doesn't look right.
The goods news is that Celas ransomware doesn't encrypt files. Other Trojans do encrypt certain files on infected computers and for this reason it usually takes longer to remove malicious files and decrypt files.
The British version is pretty much the same, except for different payment methods: Ukash and PaySafecard.
So, if you got infected with Celas ransomware, please follow the steps in the removal guide below. Normally, this malware can be removed in Safe Mode rather easily. Unfortunately, sometimes it comes bundled with other malware that locks down the computer completely. In such case, Live CD is the only option. We will show you how to remove Celas ransomware using Kaspersky Rescue Disk. Hopefully, this virus will only cost you time without taking your money too.
If you have any questions about this infection or need help removing it, please leave a comment below. Good luck!
Source: http://deletemalware.blogspot.com
Celas malware removal instructions:
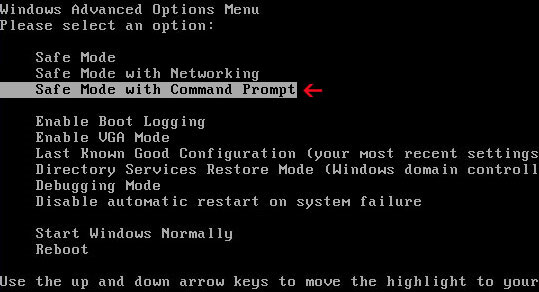
1. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode.
2. When Windows loads, the Windows command prompt will show up as show in the image below. At the command prompt, type explorer, and press Enter. Windows Explorer opens. Do not close it.

3. Then open the Registry editor using the same Windows command prompt. Type regedit and press Enter. The Registry Editor opens.

4. Locate the following registry entry:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\
In the righthand pane select the registry key named Shell. Right click on this registry key and choose Modify.

Default value is Explorer.exe.

Modified value data points to Trojan Ransomware executable file.

Please copy the location of the executable file it points to into Notepad or otherwise note it and then change value data to Explorer.exe. Click OK to save your changes and exit the Registry editor.
5. Remove the malicous file. Use the file location you saved into Notepad or otherwise noted in step in previous step.
Go back into "Normal Mode". To restart your computer, at the command prompt, type shutdown /r /t 0 and press Enter.

6. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove the leftovers of Celas ransomware from your computer.
Celas malware removal using Kaspersky Rescue Disk:
1. Download the Kaspersky Rescue Disk iso image from the Kaspersky Lab server. (Direct download link)
Please note that this is a large downloaded, so please be patient while it downloads.
2. Record the Kaspersky Rescue Disk iso image to a CD/DVD. You can use any CD/DVD record software you like. If you don't have any, please download and install ImgBurn. Small download, great software. You won't regret it, we promise.
For demonstration purposes we will use ImgBurn.
So, open up ImgBurn and choose Write image file to disc.
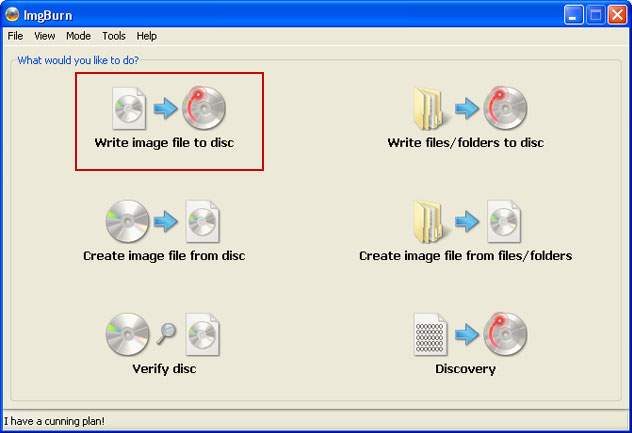
Click on the small Browse for file icon as show in the image. Browse into your download folder and select kav_rescue_10.iso as your source file.
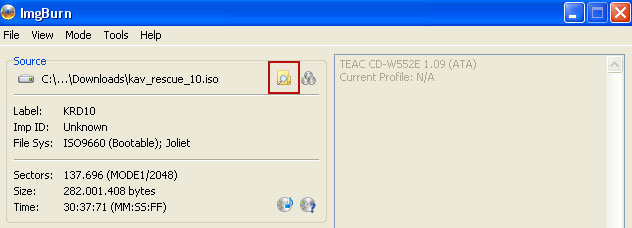
OK, so know we are ready to burn the .iso file. Simply click the Write image file to disc button below and after a few minutes you will have a bootable Kaspersky Rescue Disk 10.
3. Configure your computer to boot from CD/DVD. Use the Delete or F2, F11 keys, to load the BIOS menu. Normally, the information how to enter the BIOS menu is displayed on the screen at the start of the OS boot.
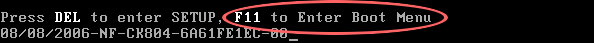
The keys F1, F8, F10, F12 might be used for some motherboards, as well as the following key combinations:
- Ctrl+Esc
- Ctrl+Ins
- Ctrl+Alt
- Ctrl+Alt+Esc
- Ctrl+Alt+Enter
- Ctrl+Alt+Del
- Ctrl+Alt+Ins
- Ctrl+Alt+S
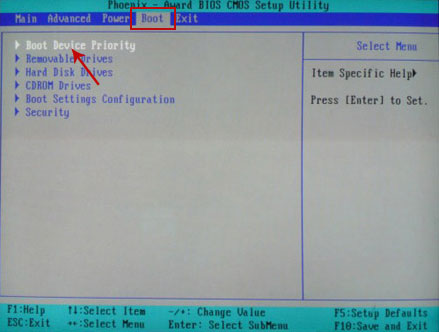
If you can't enter Boot Menu directly then simply use Delete key to enter BIOS menu. Select Boot from the main BIOS menu and then select Boot Device Priority.
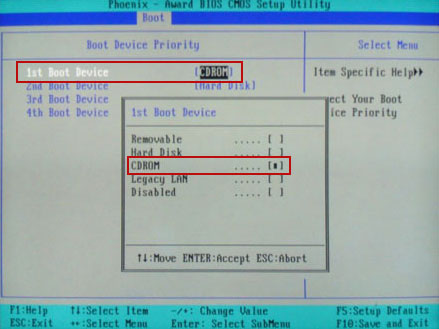
Set CD/DVD-ROM as your 1st Boot Device. Save changes and exist BIOS menu.
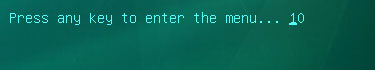
4. Let's boot your computer from Kaspersky Rescue Disk.
Restart your computer. After restart, a message will appear on the screen: Press any key to enter the menu. So, press Enter or any other key to load the Kaspersky Rescue Disk.
5. Select your language and press Enter to continue.

6. Press 1 to accept the End User License Agreement.
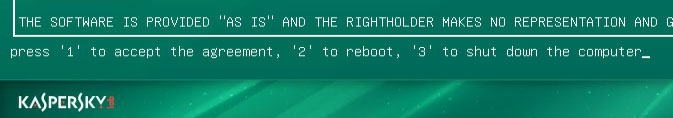
7. Select Kaspersky Rescue Disk. Graphic Mode as your startup method. Press Enter. Once the actions described above have been performed, the operating system starts.
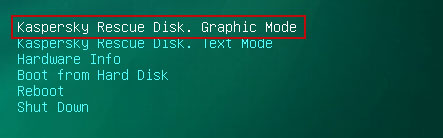
8. Click on the Start button located in the left bottom corner of the screen. Run Kaspersky WindowsUnlocker to remove Windows system and registry changes made by Celas ransomware. It won't take very long.
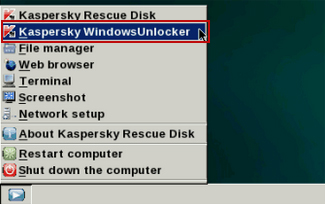
9. Click on the Start button once again and fire up the Kaspersky Rescue Disk utility. First, select My Update Center tab and press Start update to get the latest malware definitions. Don't worry if you can't download the updates. Just proceed to the next step.
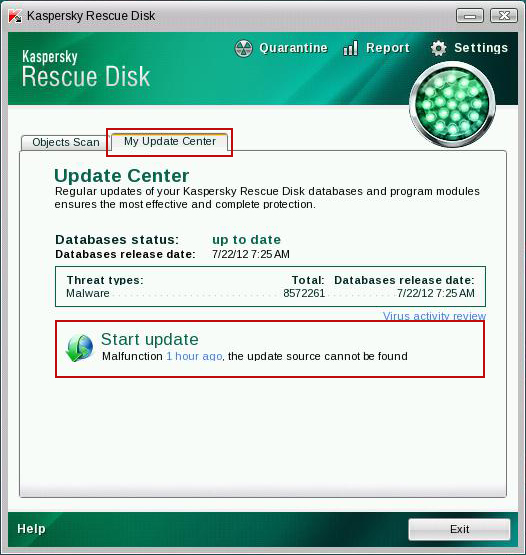
10. Select Object Scan tab. Place a check mark next to your local drive C:\. If you have two or more local drives make sure to check those as well. Then click Start Objects Scan to scan your computer for malicious software.
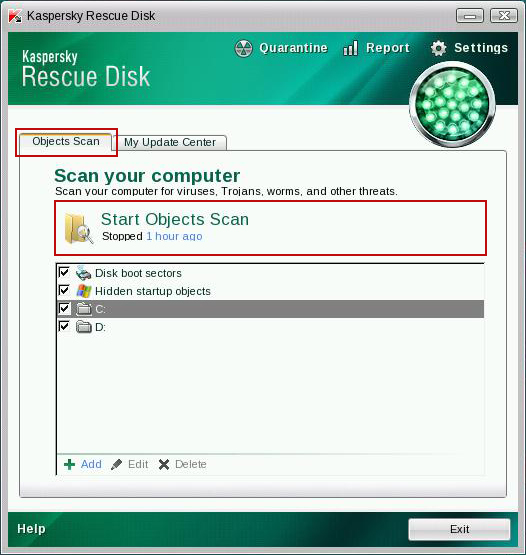
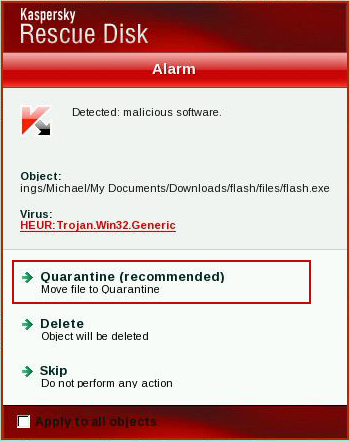
11. Quarantine (recommended) or delete every piece of malicious code detected during the system scan.
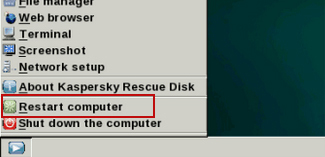
12. You can now close the Kaspersky Rescue Disk utility. Click on the Start button and select Restart computer.
13. Please restart your computer into the normal Windows mode. Download recommended anti-malware software (Spyware Doctor) and run a full system scan to remove the remnants of Celas ransomware and to protect your computer against these types of threats in the future.
Associated Celas ransomware files and registry values:
Files:
- [SET OF RANDOM CHARACTERS].exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\"Shell" = "[SET OF RANDOM CHARACTERS].exe"















0 comments:
Post a Comment