

BUNDESPOLIZEI ransomware removal instructions:
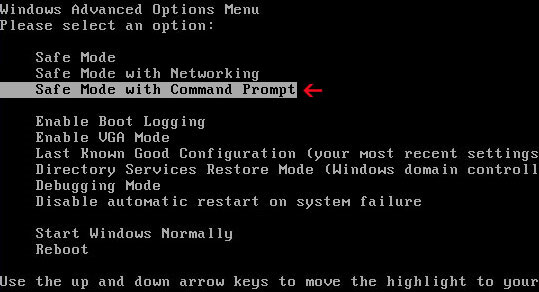
1. Reboot your computer is "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key. Login as the same user you were previously logged in with in the normal Windows mode.
2. Open Windows Registry editor using the Windows command prompt. Type regedit and press Enter. The Registry Editor opens.

3. Locate the following registry entries:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon
In the righthand pane select the registry key named Shell. Right click on this registry key and choose Modify.
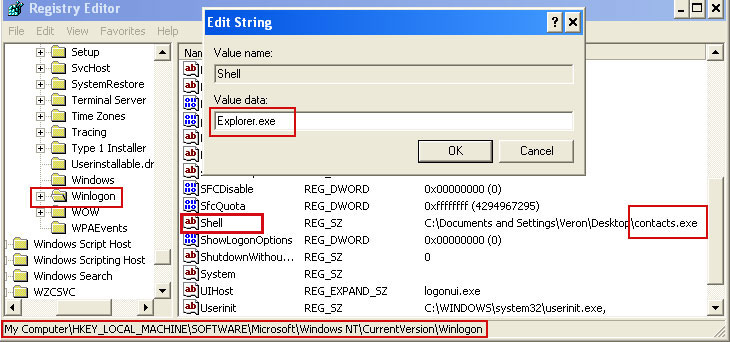
Default value is Explorer.exe.

Modified value data points to BUNDESPOLIZEI executable file.

Please note the file name, in our case it was "contacts.exe". Then change value data to Explorer.exe.
4. Choose Edit → Find (or press Ctrl+F). Registry Editor displays the Find dialog box. Type in the file name that you noted in the previous step and click the Find next button. Remove all found entries from Windows registry related to this file.

We found two additional registry keys:
HKEY_CURRENT_USER\Software\Microsoft\Search Assistant\ACMru\5603

HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\MUICache

Exit the Registry editor.
5. At the command prompt, type shutdown /r /t 0 and press Enter. It restarts computer into normal mode.

6. Download recommended anti-malware software (direct download) to remove the leftovers of this ransomware.
Read more about Trojan.Ransomware.
Associated BUNDESPOLIZEI Ransomware files and registry values:
Files:
- [RANDOM].exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon "Shell = [RANDOM].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Search Assistant\ACMru\5603 "000 = [RANDOM].exe"
- HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\MUICache "[RANDOM].exe"















0 comments:
Post a Comment