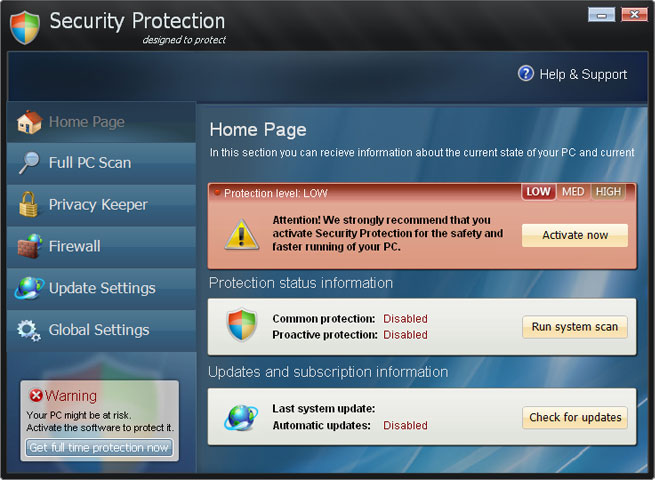
Security Protection is distributed though the use of fake online scanners; that's probably the most popular malware distribution mechanism. For example, if you search for something on Google and then click on a search result or image you are taken to a webpage which serves up a fake online scanner. It claims to detect a large number of nonexistent threats and urges you to install malware removal tool or anti-virus software. Once downloaded to your computer, Security Protection runs a fake system scan. It displays fake security alerts, pop-up windows and notifications like very one or two minutes saying that your computer is infected.
Fake Security Protection alerts:



What is more, Security Protection blocks other programs on your computer, including your web browser and takes you to a web page where you can purchase it. It displays fake notification saying that Internet Explorer or any other program is infected with W32/Blaster.worm.
iexplore.exe can not start
File iexplore.exe is infected by W32/Blaster.worm
Please activate Malware Protection to protect your computer.

The good news is that your computer is not infected with W32/Blaster worm and other viruses as this rogue programs claims. However, you should remove Security Protection from your computer as soon as possible. Just restart your computer in Safe Mode with Networking, download anti-malware software and run a full system scan.
OPTIONAL: In case you can't boot your PC in Safe Mode with Networking or you can't delete the malicious files manually, you can use this code SL55J-T54YHJ61-YHG88 and any email to register the rogue application in order to stop the fake security alerts.

Once this is done, you are free to install recommended anti-malware software (direct download) to remove the rogue anti-virus program from your computer properly. If you need help in removing Security Protection from your computer, please leave a comment below. Additional information about this malware and comments are welcome too. Good luck and be safe online.
Related malware:
Security Protection removal instructions (in Safe Mode with Networking):
1. Reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key. Read more detailed instructions here: http://www.computerhope.com/issues/chsafe.htm
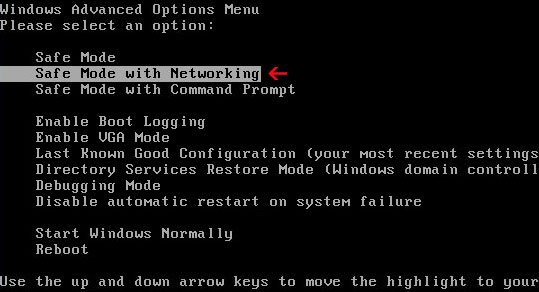
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove this rogue anti-virus program from your computer.
NOTE: in some cases the rogue program may block anti-malware software. Before saving the selected program onto your computer, you may have to rename the installer to iexplore.exe or winlogon.exe With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Security Protection associated files and registry values:
Files:
Windows XP:
- C:\Documents and Settings\All Users\Application Data\defender.exe
- C:\ProgramData\defender.exe
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Security Protection"















0 comments:
Post a Comment