This rogue security program goes by many different names listed below.
- XP Antispyware 2012
- XP Antivirus 2012
- XP Security 2012
- XP Home Security 2012
- XP Internet Security 2012
- XP Total Security 2012


While running, this rogue antivirus constantly displays fake security alerts and notifications about serious security threats every few minutes.

Privacy threat!
Spyware intrusion detected. Your system is infected. System integrity is at risk. Private data can be stolen by third parties, including credit card details and passwords. Click here to perform a security repair.

What is more, the fake AV may open up Internet Explorer and load random pornographic websites. It could be anything actually, fake pharmacy or health care web pages, gay porn and similar websites. However, most of the time it just blocks other applications, including Internet Explorer, stating that it's infected with Trojan-BNK.Win32.Keylogger.gen.
It also displays a fake Internet Explorer Security Alert which basically says that pretty much every website that you're about to visit is malicious and may infect your computer. It blocks other web browsers too.

This rogue antivirus application also displays a fake Windows Security Center window which states that your computer is not protected and that you should install anti-virus software. Of course, it promotes rogue anti-virus applications, XP Antispyware 2012, XP Security 2012 and others.

XP Antispyware 2012 prompts the users of the infected computer to register the program in order to remove the threats which do not even exist. Here's a screenshot of what the fake payment page looks like:

Quick removal:
1. Update: You can use this debugged serial key 9443-077673-5028 or 3425-814615-3990 to register the rogue application in order to stop the fake security alerts. Just click the Registration button and then select "Activate manually". Don't worry, this is completely legal. If the debugged serial keys do not work anymore, please follow the removal instructions below.

Once this is done, you are free to install anti-malware software and remove the rogue anti-virus program from your computer properly.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
XP Antispyware 2012, XP Internet Security 2012 removal instructions are outlined below in case the . If you need help removing this annoying malware from your computer just leave a comment below. And if you have any additional information that you think may help our readers, just let us know. Good luck and be safe online!
Alternate removal instructions:
Make sure that you can see hidden and operating system protected files in Windows. For more in formation, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmarks from the checkboxes labeled:
- Hide extensions for know file types
- Hide protected operating system files

1. Go into C:\Documents and Settings\[UserName]\Local Settings\Application Data\ folder.
For example: C:\Documents and Settings\Michael\Local Settings\Application Data\

2. Find hidden executable file in this folder. In our case it was called wmi.exe, but I'm sure that the file name will be different in your case. Rename wmi.exe to virus.exe and click Yes to confirm file rename. Then restart your computer.

3. After a restart, copy all the text in bold below and paste to Notepad.
Windows Registry Editor Version 5.00
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
4. Save file as fix.reg to your Desktop. NOTE: (Save as type: All files)
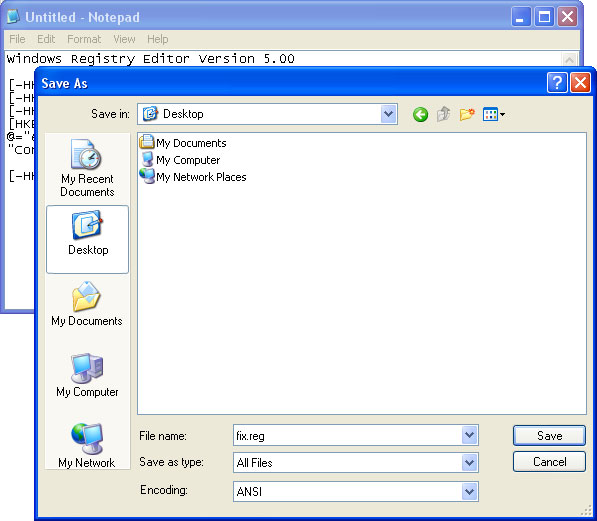
5. Double-click on fix.reg file to run it. Click "Yes" for Registry Editor prompt window. Then click OK.
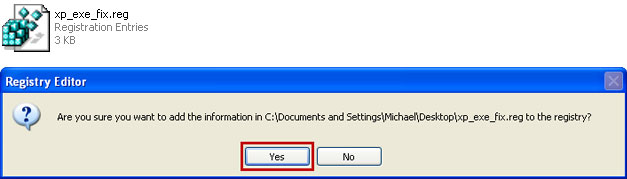
6. Open Internet Explorer. Download xp_exe_fix.reg and save it to your Desktop. Double-click on xp_exe_fix.reg to run it. Click "Yes" for Registry Editor prompt window. Click OK.
7. Download recommended anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
NOTE: With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
XP Antispyware 2012, XP Internet Security 2012, XP Security 2012 removal instructions:
1. Click Start->Run or press WinKey+R. Type in "command" and press Enter key.

2. In the command prompt window type "notepad" and press Enter key. Notepad will come up.

3. Copy all the text in blue color below and paste to Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\secfile]
[-HKEY_CLASSES_ROOT\secfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
4. Save file as fix.reg to your Desktop. NOTE: (Save as type: All files)

5. Double-click on fix.reg file to run it. Click "Yes" for Registry Editor prompt window. Then click OK.
6. Download recommended anti-malware software (direct download) and run a full system scan to remove this virus from your computer.
NOTE: With all of these tools, if running Windows 7 or Vista they MUST be run as administrator. Launch the program and follow the prompts. Don't forget to update the installed program before scanning.
Associated XP Antispyware 2012, XP Internet Security 2012, XP Security 2012 files and registry values:
Files:
- C:\Documents and Settings\All Users\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\[UserName]\Application Data\[SET OF RANDOM CHARACTERS]
- C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe
- C:\Documents and Settings\[UserName]\Templates\[SET OF RANDOM CHARACTERS]
- C:\Documents And Settings\[UserName]\Local Settings\Temp\[SET OF RANDOM CHARACTERS]
- HKEY_USERS\.DEFAULT\Software\Microsoft\Internet Explorer\BrowserEmulation "TLDUpdates" = '1'
- HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" -a "%1" %*'
- HKEY_CURRENT_USER\Software\Classes\exefile\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exee" -a "%1" %*'
- HKEY_CLASSES_ROOT\.exe\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" -a "%1" %*'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\open\command "(Default)" = '"%LocalAppData%\kdn.exe" -a "C:\Program Files\Mozilla Firefox\firefox.exe"'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\FIREFOX.EXE\shell\safemode\command "(Default)" = '"%LocalAppData%\kdn.exe" -a "C:\Program Files\Mozilla Firefox\firefox.exe" -safe-mode'
- HKEY_LOCAL_MACHINE\SOFTWARE\Clients\StartMenuInternet\IEXPLORE.EXE\shell\open\command "(Default)" = '"C:\Documents and Settings\[UserName]\Local Settings\Application Data\[3 RANDOM CHARACTERS].exe" -a "C:\Program Files\Internet Explorer\iexplore.exe"'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "AntiVirusOverride" = '1'
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center "FirewallOverride" = '1'















0 comments:
Post a Comment