As far as I can tell, TR/ATRAPS.Gen2 is distributed in various ways, using infected websites, malicious emails and even game cracks or free premium account generators. Just because a program says it’s a game and it looks like a game, it is not necessarily a game and it might actually be a Trojan horse. In fact some types of Trojan horse software are programs that masquerade as anti-virus software - although they’re actually infecting you with viruses and are the very thing they claim to be protecting you against! Learn more: Rogue Antivirus software.
Access to file containing the virus or unwanted program 'TR/ATRAPS.Gen2' was blocked.
As with types of viruses and malware, not all Trojan horses are the same either and they are split into categories depending on how they access your computer’s system and the type of damage they cause. TR/ATRAPS.Gen2 may be used to steal sensitive information, display ads on your computer or redirect your web browser to infected websites. It can also download additional malware modules onto your computer. As you can see, this Trojan horse is really well designed and coded. Detection ratio speaks for itself, it's usually below 50%, see this. I've seen some fresh samples that were detected by only two or three antivirus programs which means, this malware uses advanced techniques to bypass antivirus protection.
Unfortunately for computer users, whether it’s just you at home alone on your laptop or a network administrator in a busy corporate environment, attacks by Trojan Horses are increasing not only in amount but in sophistication too. They affect users in all countries across the globe and no one is immune so how do you protect yourself from falling victim?
The thing to remember is that just as the people of Troy were fooled by the Greeks into letting them into their city to capture it, computer Trojan horses operate on the same principle. An attacker will try to convince you to run TR/ATRAPS.Gen2 on your computer by making you think it’s perfectly safe. It is for this reason that most Trojan Horses are hidden inside games or other popular downloads.
Luckily a good (genuine!) anti-malware program will detect and delete the TR/ATRAPS.Gen2 virus before you have a chance to run them, thus installing them on your PC. It goes without saying, therefore, that you should always have decent anti-malware software installed and you should also make sure it is the most up to date version.
You should also take care not to do as the Trojans did and let ‘the horse’ in. This means never clicking on an email attachment from a sender you do not know and not downloading or installing games, anti-viruses or other programs from sources that you do not trust or are unsure about. To remove TR/ATRAPS.Gen2 from your computer, please follow the removal instructions below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
TR/ATRAPS.Gen2 removal instructions:
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
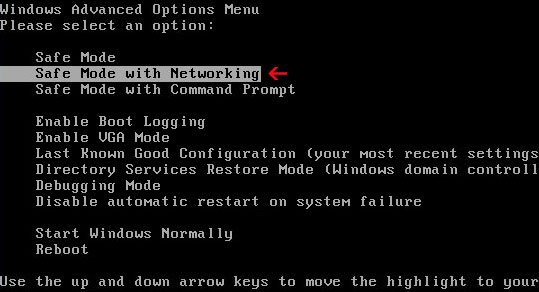
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove TR/ATRAPS.Gen2 from your computer.
3. Reboot your computer as normal. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

4. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.

















0 comments:
Post a Comment