Cyber crooks distribute this Trojan in every possible way to reach as many PC users as possible. Usually, they use hacked websites. They may also send you an email with an infected attachment, which once clicked upon will run the Trojan horse and infect your PC or laptop. For example let’s say the email has a game attached to it – it looks great fun and you can’t wait to get playing. So what do you do? You run the .exe file in order to install the game on your computer but bingo – you’ve just installed the Luhe.Sirefef.A Trojan.
What the Trojan horse will then do is to start over-writing certain sections of your hard drive thus corrupting your files and data. Very often, this virus is detected in services.exe and other system files. The only small silver lining to this cloud is that Trojan horses are not actually viruses (although many people tend to think of them as such). A computer virus will replicate itself but a Trojan horse will not. The good thing about this is that Trojan horses only wreak their damage if they are given the opportunity to run and the majority of good anti-malware software will be able to detect and delete Trojan horse software before you have a chance to do anything with it.
So what is the moral of this story that started off with a Greek army and ended up with data corruption? The number one rule is the same that should be applied when protecting yourself from all forms of malicious software and viruses: make sure you have a well-known brand of anti-malware software installed on your computer to stop Luhe.Sirefef.A in its track. And make sure it’s the latest version too.
Furthermore, don’t open programs or download software unless you are 100% sure that they come from a reliable and trusted source – particularly if they have been sent to you in the form of an executable file attached to an email. And if you don’t know the sender; then definitely don’t touch it. Remember that this is exactly the way Trojan horses work – don’t make the same mistake as the people of Troy did by letting it through the ‘gates’ of your computer. If you antivirus was unable to disinfect Luhe.Sirefef.A, please follow the removal instructions below on how to eliminate this and any other threat from your computer. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Luhe.Sirefef.A removal instructions:
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
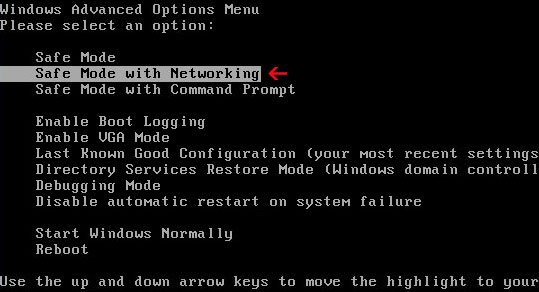
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Download recommended anti-malware software (direct download) and run a full system scan to remove this Trojan from your computer.
3. Reboot your computer as normal. Download and run TDSSKiller. Press the button Start scan for the utility to start scanning.

4. Wait for the scan and disinfection process to be over. Then click Continue. Please reboot your computer after the disinfection is over.

















0 comments:
Post a Comment