You really shouldn't browse such websites, because they are usually less than legal. Anyway, I'm sure you have seen one of these infections in the past. The problem is that they can look very convincing and hold the system hostage. Internet Security 2012 designed to protect wouldn't allow certain programs to run claiming they are infected, even though this is not the case. The fake AV infection blocks legit anti-virus software and may even hide certain files to make it look like your computer is really messed up.

Once executed, Internet Security displays a bunch of fake security warnings and notifications. The fake warnings has several sings that they are not legitimate. Some of the statements just don't make sense, full of misspellings. For example. the rogue program was tellin me that 'iexplore.exe' was a virus and had been prevented from running.
iexplore.exe can not start
File iexplore.exe is infected by W32/Blaster.worm.
Please activate Internet Security 2012 to protect your computer.

Well, actually, it's a perfectly legitimate Windows file and even though it can get infected, this isn't the case. Do not follow instructions on screen and do not purchase it. Cyber crooks make money from people who buy the bogus software. Gathered information, including your name, address and credit card details, can put you at risk of identity theft. If you mistakenly thought it was a real and bought it, please contact your credit card company and dispute the charges.
Booting your computer in safe mode is a good first start when it comes to dealing with fake antivirus programs. Internet Security 2012 won't get a chance to load and you will be able to remove offending files manually. After rebooting, you still need to scan your computer with recommended anti-malware software. This is an important step to take after manually cleaning up an infection to ensure that nothing has been missed. To remove Internet Security 2012 from your computer, please follow the removal instructions below. Of course, nothing is ever that simple. So, if you need help removing this malware, please leave a comment below. Good luck and be safe online!
Manual activation and Internet Security 2012 removal:
1. Choose to remove threats and manually activate the rogue program. Enter one of the following codes
Y68REW-T76FD1-U3VCF5A
Y86REW-T75FD5-U9VBF4A
Y76REW-T65FD5-U7VBF5A
Y86REW-T75FD5-9VB4A
SL55J-T54YHJ61-YHG88
(and any email) to activate Internet Security 2012.

2. Then download recommended anti-malware software (direct download) and run a full system scan to remove this rogueware from your computer.
Internet Security 2012 removal instructions in Safe Mode with Networking:
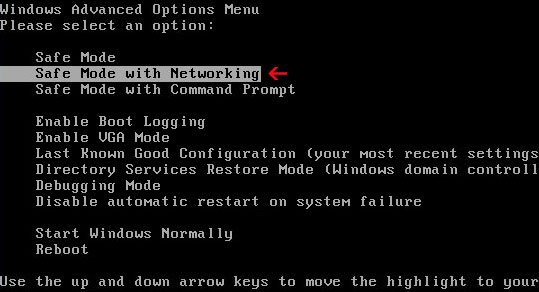
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Open Internet Explorer and download TDSSKiller. Run the utility and click Start Scan to anti-rootkit scan.
3. Then recommended anti-malware software (direct download) and run a full system scan to remove the rogue virus from your computer.
Manual Internet Security 2012 removal instructions:
1. Right click on the "Internet Security 2012" icon, click Properties in the drop-down menu, then click the Shortcut tab.

In the Target box there is a path to the malicious file.

NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmark from the checkbox labeled:
- Hide extensions for known file types
- Hide protected operating system files
Click OK to save the changes. Now you will be able to see all files and folders in the Application Data/Program Data directory.
3. Rename malicious process.
File location, Windows XP:
C:\Documents and Settings\All Users\Application Data\isecurity.exe
File location, Windows Vista/7:
C:\ProgramData\isecurity.exe

Rename isecurity to virus or whatever you like. Example:

4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.

6. Download recommended anti-malware software (direct download) and run a full system scan to remove Internet Security 2012 virus from your computer. That's it!
Internet Security 2012 associated files and registry values:
Files:
- C:\ProgramData\isecurity.exe (Win Vista/7)
- C:\Documents and Settings\All Users\Application Data\isecurity.exe (Win XP)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Internet Security 2012"















0 comments:
Post a Comment