First of all with RCMP Ukash ransomware, the clue is really in the title. It’s software that holds you to ransom and demands a payment. Doesn’t sound very nice does it but how can a simple piece of computer software kidnap a human, and where do the police come into all of this?!
Normally when a computer virus attacks your PC or laptop it’s because you opened an infected email attachment or file. RCMP Ukash virus is slightly different; known as a ‘drive-by virus’ it can install itself on your machine simply by you visiting a website that has been compromised. What then happens is that you’ll be innocently looking at a friend’s photos on Facebook or shopping online and your computer will suddenly freeze. And this isn’t any normal case of having too many web browsers open or something crashing. You will then see a pop-up screen or message which for all intents and purposes seems to have come either from The FBI, if you’re in the United States, The Metropolitan Police, if you’re in the UK, or from the Royal Canadian Mounted Police if you’re in Canada.
So what does this window say? It will accuse you of having violated federal law for one thing and claim that you’ve either been caught looking at under age porn or have been known to have downloaded illegal music, software, movies or TV shows. It will also give you a handy list of what the fines and penalties for your ‘crime’ is and then give you comprehensive instructions of how to pay your fines, using a pre-paid card, so that you will ‘not have criminal charges filed against you’.
Some of these RCMP Ukash ransomware viruses even have the ability to turn your computer’s webcam on so that it takes a picture of you and displays it on your screen, making you think that you are somehow being watched or recorded. It is pretty scary stuff and the designs of these pages are often extremely sophisticated and believable. Especially if you may just have happened to download season six of your favourite television show! And don’t think that clicking the little ‘x’ in the corner of the window will get rid of the scary message: it won’t. Your computer will be frozen and seemingly the only way out of this mess is to pay the fine – which can often be an extortionate amount running into hundreds or even thousands of dollars.
What is important to know here is that no reputable national or international law enforcement agency would ask you to pay a fine or a penalty online – both The FBI and The Royal Canadian Mounted Police in Canada have stated this in reference to ransomware crimes, of which they are increasingly inundated with reports of. Unfortunately malicious software is a lucrative business and while there are people out there who will pay the financial fines, the hackers will keep on developing more and more devious techniques to fool us and get us to hand over our hard earned cash online.
So how can you protect yourself from this extremely unpleasant crime? First of all ensure that you have a reputable and top quality antivirus or security software installed on your PC and make sure that’s it’s always updated to the latest version. Secondly do not click on links that you don’t trust, or know – you could be just steps away from having malware installed on your computer.
Some ransomware viruses also hold your documents to ransom; freezing your computer or encrypting files so to minimize any damage or loss of data make sure you back up your files on a very regular basis.
And if you are unfortunate enough to fall victim to a ransomware or police-themed ransomware virus, whatever you do, don’t pay any money or enter any personal details! These sorts of viruses are notoriously difficult for even fairly technical home users to remove, but you can still attempt to remove the RCMP Ukash virus by following the removal guide below. The virus is not the same for everyone, so I can't guarantee that this fix will work for you, just give it a try.
One last thing to remember is that even if the virus has been removed and your computer fixed, the malware may still be running in the background so contact your bank and credit card companies, change your passwords and delete any non-essential personal details or documents that you may have stored on your PC. Finally, scan your computer with recommended anti-malware software to remove related malware from your computer. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: RCMP Ukash virus removal instructions using System Restore in Safe Mode with Command Prompt:
1. Reboot your computer is Safe Mode with Command Prompt. As the computer is booting tap the F8 key continuously which should bring up the Windows Advanced Options Menu as shown below. Use your arrow keys to move to Safe Mode with Command Prompt and press Enter key.
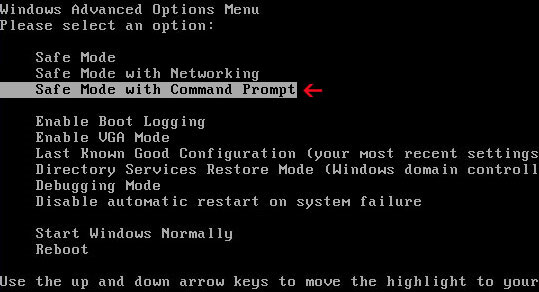
2. Make sure you log in to an account with administrative privileges (login as admin).
3. Once the Command Prompt appears you have few seconds to type in explorer and hit Enter. If you fail to do it within 2-3 seconds, the RCMP Ukash virus will take over and will not let you type anymore.
4. If you managed to bring up Windows Explorer you can now browse into:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
6. Download recommended anti-malware software (direct download) and run a full system scan to remove this virus.
Method 2: RCMP Ukash virus removal instructions using System Restore in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the F8 key continuously which should bring up the Windows Advanced Options Menu as shown below. Use your arrow keys to move to Safe Mode and press Enter key.
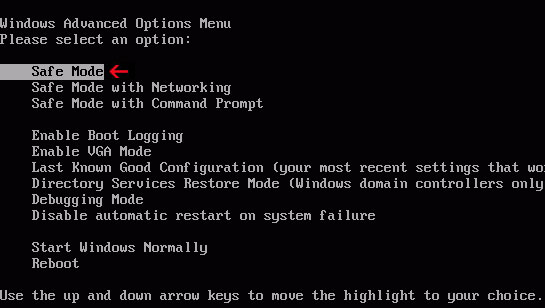
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for system restore. Or you can browse into the Windows Restore folder and run System Restore utility from there:
- Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
- Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
4. Select a restore point from well before the RCMP virus appeared, two weeks should be enough.
5. Restore it. Please note, it can take a long time, so be patient.
6. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
7. At this point, download recommended anti-malware software (direct download) and run a full system scan to remove the virus.
Method 3: RCMP Ukash virus removal instructions using MSConfig in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the F8 key continuously which should bring up the Windows Advanced Options Menu as shown below. Use your arrow keys to move to Safe Mode and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for "msconfig". Launch the application. If you're using Windows XP, go to Start then select Run.... Type in "msconfig" and click OK.
3. Select Startup tab. Expand Command column and look for a startup entry that launches randomly named file from %AppData% or %Temp% folders using rundll32.exe. See example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
4. Disable the malicious entry and click OK to save changes.
5. Restart your computer. This time Start Windows normally. Hopefully, you won't be prompted with a fake RCMP screen.
6. Finally, download recommended anti-malware software (direct download) and run a full system scan to remove the virus.
Method 4: Manual RCMP Ukash virus removal instructions Safe Mode (requires registry editing) :
1. Unplug your network cable and manually turn your computer off. Reboot your computer in Safe Mode. As the computer is booting tap the F8 key continuously which should bring up the Windows Advanced Options Menu as shown below. Use your arrow keys to move to Safe Mode and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. When Windows loads, open up Windows Registry Editor.
To do so, please go to Start, type "registry" in the search box, right click the Registry Editor and choose Run as Administrator. If you are using Windows XP/2000, go to Start → Run... Type "regedit" and hit enter.
3. In the Registry Editor, click the [+] button to expand the selection. Expand:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
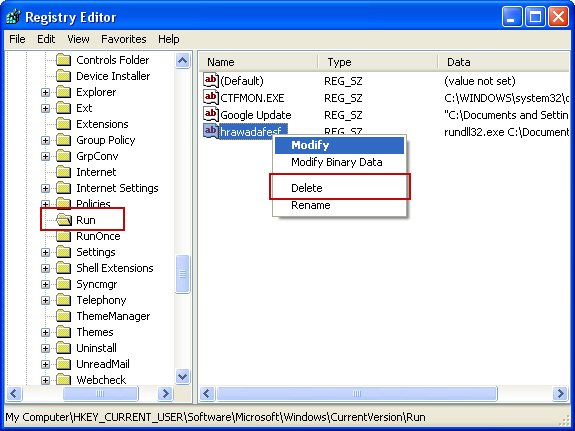
Look on the list to the right for an randomly named item. Write down the file location. Then right click the randomly named item and select Delete. Please note that in your case the file name might be different. Close Registry Editor.
In our case the malicious file (pg_0rt_0p.exe) was located in Application Data folder. So, we went there and simply deleted the file. We're running Windows XP.
File location: C:\Documents and Settings\Michael\Application Data\
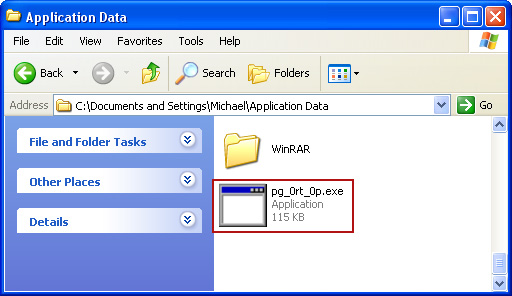
If you are using Windows Vista or Windows Seven, the file will be located in %AppData% folder.
File location: C:\Users\Michael\AppData\Romaming\
Finally, go into Windows Temp folder %Temp% and click Date Modified so the newest files are on top. You should see an exe file, possibly with the name pg_0rt_0p.exe (in our case it was exactly the same), but it may be different in your case. Delete the malicious file.
One more thing, check your Programs Startup list for the following entry:
[UserPATH]\Programs\Startup\ctfmon.lnk - C:\Windows\system32\rundll32.exe pointing to [UserPATH] \Temp\wpbt0.dll,FQ10 (or FQ11)
In our case it was ctfmon.lnk pointing to malicious file which then loads the fake ransom warning. Please note that in your case the file name might be different, not necessarily ctfmon.lnk. Simply disable or remove (if possible) such entry and restart your computer.
4. Restart your computer into "Normal Mode" and scan the system with legitimate anti-malware software.
5. Download recommended anti-malware software (direct download) and run a full system scan to remove the remnants of virus.
















0 comments:
Post a Comment