So how can you tell the difference between genuine antivirus software and malicious fake antivirus software? And what should you do if you suspect that your computer has been infected? Read on and we’ll take a look at how even if you are sceptical you can still fall victim to the scammers.
Have you ever been surfing the web when suddenly a pop-up window or alert appears on your screen either telling you that you have unnecessary items on your PC that are slowing it down, or even more worrying, that you’ve been infected with a virus? This alert may look like it comes from your antivirus software provider or it may come from one you’re not aware of – but regardless it looks real and anyway, why should you think otherwise?
However, even if you are suspicious or even if you think, ‘I’ll deal with that later’ you may be tempted to click the little ‘x’ in the right hand corner of the pop-up to get rid of it. But stop – don’t because even ‘getting rid’ of the pop-up can cause untold trouble and computer issues. You may have now started seeing pop-up adverts all over your screen, maybe your screen has frozen, perhaps you can’t access your programs or documents. What has happened is that your whole computer has been disabled.
Some hackers do this purely because they can – we can only assume it’s their version of having ‘fun’, however the majority of hackers are running a scam and want to trick you into buying fake antivirus, in this case Internet Security 2014 designed to protect. Again, you’re happily browsing the internet or busy working when, hello again , our friend the virus warning alert pops up. Just as before, it may look like it’s come from your own antivirus company or it may be one you don’t recognise. You might be tempted to let it scan and clean your system for you but what it will actually be doing is simply showing you a fake scanning screen – the result of which will be to pronounce that, yes, you have been infected by Win32/Blaster.Worm and hundreds of other viruses.
What you will then see is a window from Internet Security 2014 who will attempt to frighten you into paying to have your computer ‘cleaned’ by asking if you want them to get rid of the virus or if you want to continue working on your infected computer. Of course, most of us will panic and hand over our credit card details. So now we’ve got two issues: one is that we’re paying for something that wasn’t a problem in the first place and, two, we’re handing over sensitive information to a scammer.
And it gets worse because some fake antivirus software even installs rootkits onto your computer so that it can log your key strokes and/or take screen shots so that your passwords, log-ins, credit card details and other private data is collected. The hackers will then use this information to plunder your bank account, spend on your credit card or commit identity theft. Alternatively they may sell the information on to a third party. Recently, scammers started to use Sirefef malware to block genuine malware removal programs.
A rogue virus alert comes from a program called Internet Security 2014, which is malware that takes over the control of your computer. So how do you stop yourself downloading rogue software unwittingly? The first rule is not to open any email attachment or click a link in an email that comes from someone you don’t know. No matter how enticing the title, do not be tempted. You might think it’s a harmless link that just wants to direct you to a website that’s selling something but it could actually be a way of installing malware on your computer. And definitely don’t click on pop-ups advertising antivirus software!
Last, but not least, the fake antivirus program blocks web browsers and Windows utilities, even Notepad to protect itself from being removed. It simply annouces that your web browser or any other program ins infected with Win32.Blaster.Worm. As an additional protection module Sirefef may be used making the infection even more complicated to fix. To remove Internet Security 2014 malware from your computer, please follow the removal guide below. If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Manual activation and Internet Security 2014 removal:
1. Choose to remove threats and manually activate the rogue antivirus program. Enter one of the following codes:
Y68REW-T76FD1-U3VCF5A
Y86REW-T75FD5-U9VBF4A
Y76REW-T65FD5-U7VBF5A
Y86REW-T75FD5-9VB4A
SL55J-T54YHJ61-YHG88
(and fake email) to activate Internet Security 2014.

2. Then download recommended anti-malware software (direct download) and run a full system scan to remove this malware from your computer.
Internet Security 2014 removal instructions in Safe Mode with Networking:
1. Please reboot your computer is "Safe Mode with Networking". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Networking" and press Enter key.
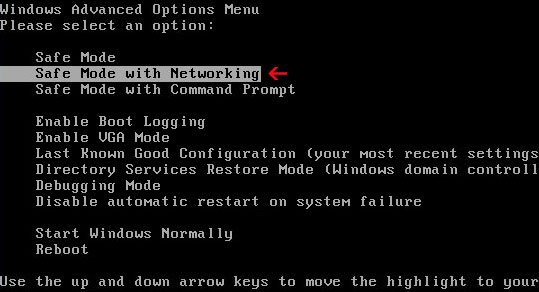
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Open Internet Explorer and download TDSSKiller. Run the utility and click Start Scan to anti-rootkit scan.
3. Then recommended anti-malware software (direct download) and run a full system scan to remove the rogue virus from your computer.
Manual Internet Security 2014 removal instructions:
1. Right click on the "Internet Security 2014" icon, click Properties in the drop-down menu, then click the Shortcut tab.

In the Target box there is a path to the malicious file.

NOTE: by default, Application Data folder is hidden. Malware files are hidden as well. To see hidden files and folders, please read Show Hidden Files and Folders in Windows.
Under the Hidden files and folders section, click Show hidden files and folders, and remove the checkmark from the checkbox labeled:
- Hide extensions for known file types
- Hide protected operating system files
Click OK to save the changes. Now you will be able to see all files and folders in the Application Data/Program Data directory.
3. Rename malicious process.
File location, Windows XP:
C:\Documents and Settings\All Users\Application Data\amsecure.exe
File location, Windows Vista/7:
C:\ProgramData\amsecure.exe

Rename amsecure to virus or whatever you like. Example:

4. Restart your computer. The malware should be inactive after the restart.
5. Open Internet Explorer and download TDSSKiller. This malware usually (but not always) comes bundled with TDSS rootkit. Removing this rootkit from your computer is very important (if exists). Run TDSSKiller and remove the rootkit.
6. Download recommended anti-malware software (direct download) and run a full system scan to remove Internet Security 2014 virus from your computer.
Internet Security 2014 associated files and registry values:
Files:
- C:\ProgramData\amsecure.exe (Win Vista/7)
- C:\Documents and Settings\All Users\Application Data\amsecure.exe (Win XP)
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "Internet Security 2014"


















0 comments:
Post a Comment