Whilst being physically kidnapped is probably not a major concern for most people reading this (unless you’re the child of a high profile celebrity, in which case, ‘hi’!) most of us probably don’t realize that our computers – and our personal files and documents - can be hijacked or kidnapped too.
We’re all aware of computer viruses and, yes, they can be very problematic but there’s now an even more worrying trend in the world of computer crime to be aware of and that’s ransomware – or, as it can also be called, scareware, cryptoviruses, cryptotrojans and cryptoworms.
So what is ransomware, and in particular the United States Courts ransomware, how does it find its way onto our computers and how can we get rid of it if we’re unfortunate enough to fall prey to it?
As the name suggests, the United States Courts virus infects your computer, holds your personal data and documents for ransom and then asks you to pay in order for them to be released. It falls into the category of a drive-by virus because it’s malware that has installed itself on your PC or laptop without your knowledge or permission when you visited an infected or compromised website.
For example, there is a fairly recent malware called Reveton which is a good example of law enforcement ransomware. Let’s say you’re using your computer, innocently browsing the web, doing some work, researching vacation destinations…and suddenly your computer freezes and a message from your local police force or national law agency or in this case United States Courts displays on your screen. This message will look like the real deal with logos and authentic sounding wording. It will tell you that you’ve been caught viewing, accessing, storing or downloading illegal content on your computer - and it will ask you to pay a fine in order for your PC to be unfrozen. The fake messages says:
United States CourtsThe fake message also warns that you have only 48 hours to pay the 'fine' which is $300 or some times even more. The 'fine' can be paid using MoneyPak.
YOUR COMPUTER HAS BEEN LOCKED
Criminal Case NO. 4:12CV072011
Illegally downloaded material (MP3's, Movies or Software) has been located on your computer.
By downloading or uploading, those files have been reproduced, thereby involving a criminal offense under 17 U.S.C.A. SS506(a) and 18 USCA SS2319 (2)(A)(B).
. . .
All of your files have been encrypted, any attempt to unlock your computer by yourself, will result in loss of all your data.
This program is maintained by the Administrative Office of the U.S. Courts on behalf of the Federal Judiciary.
Naturally this is extremely worrying and your first instinct is to panic and search your memory for what website or content could possibly have triggered such a message. And your second instinct might be to pay up – either because you have looked at adult content recently – or whether you have or haven’t, are too embarrassed to seek help from a computer professional. Using something that potentially could cause emotional distress or cause issues in a relationship is exactly what the cyber criminals want as they hope to get you over a barrel.
These days the United States Courts virus is becoming even more sophisticated as it knows which country you are in and will display a message in your local language. There have even been reports of ransomware and other malware that have personalized voice messages and other sound effects, as the hackers tighten their grip and try to make their scams even more convincing. Not to mention that the virus may turn on your web cam and take a picture of you.
So what should you do if you’re the victim and your PC has been infected by the United States Courts MoneyPak virus? Number one: do not pay. Not only are you helping bank roll a scam (some of these criminals earn hundreds of thousand dollars a month thanks to their malware) but there’s no actual guarantee that they will unlock your system and release your files once you’ve paid; after all these are hardly the most trustworthy of people and there have been many reports of the hacker simply receiving payment and then moving on to their next victim without bothering to return your computer back to normal.
Your best bet is to follow the United States Courts virus removal guide below or to take your computer to a known local computer store and ask them to take a look at it and try and unlock it, or alternatively you could call your antivirus software program’s customer help desk as they should be able to advise which strain of ransomware has infected you and will be hopefully able to give you a step by step guide to removing it.
And on that note, let’s just impress upon how important it is to have reputable and up to date antivirus software installed on your computer! If you have any questions, please leave a comment below. Good luck and be safe online!
Written by Michael Kaur, http://deletemalware.blogspot.com
Method 1: The United States Courts virus removal instructions using System Restore in Safe Mode with Command Prompt:
1. Reboot your computer in "Safe Mode with Command Prompt". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode with Command Prompt" and press Enter key.
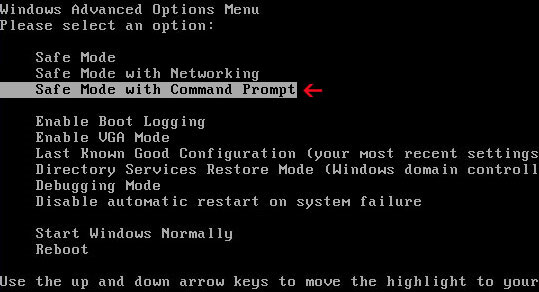
2. Make sure you log in to an account with administrative privileges (login as admin).
3. Once the Command Prompt appears you have few seconds to type in explorer and hit Enter. If you fail to do it within 2-3 seconds, the United States Courts virus will take over and will not let you type anymore.
4. If you managed to bring up Windows Explorer you can now browse into:
- Win XP: C:\windows\system32\restore\rstrui.exe and press Enter
- Win Vista/Seven: C:\windows\system32\rstrui.exe and press Enter
6. Download recommended anti-malware software (direct download) and run a full system scan to remove the virus.
Method 2: The United States Courts virus removal instructions using System Restore in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.
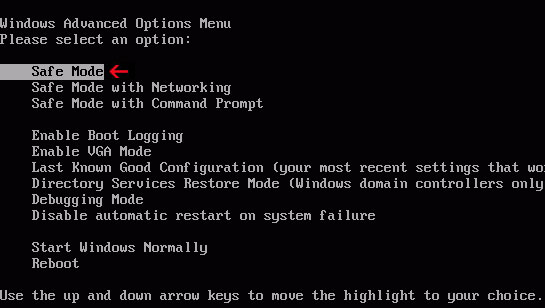
NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for "system restore". Or you can browse into the Windows Restore folder and run System Restore utility from there:
- Win XP: C:\windows\system32\restore\rstrui.exe double-click or press Enter
- Win Vista/7/8: C:\windows\system32\rstrui.exe double-click or press Enter
4. Select a restore point from well before the United States Courts virus appeared, two weeks should be enough.
5. Restore it. Please note, it can take a long time, so be patient.
6. Once restored, restart your computer and hopefully this time you will be able to login (Start Windows normally).
7. At this point, download recommended anti-malware software (direct download) and run a full system scan to remove the virus.
Method 3: The United States Courts virus removal instructions using MSConfig in Safe Mode:
1. Power off and restart your computer. As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. Once in there, go to Start menu and search for "msconfig". Launch the application. If you're using Windows XP, go to Start then select Run.... Type in "msconfig" and click OK.
3. Select Startup tab. Expand Command column and look for a startup entry that launches randomly named file from %AppData% or %Temp% folders using rundll32.exe. See example below:
C:\Windows\System32\rundll32.exe C:\Users\username\appdata\local\temp\regepqzf.dll,H1N1
4. Disable the malicious entry and click OK to save changes.
5. Restart your computer. This time Start Windows normally. Hopefully, you won't be prompted with a fake United States Courts screen.
6. Finally, download recommended anti-malware software (direct download) and run a full system scan to remove the United States Courts virus.
Method 4: Manual United States Courts virus removal instructions Safe Mode (requires registry editing) :
1. Unplug your network cable and manually turn your computer off. Reboot your computer in "Safe Mode". As the computer is booting tap the "F8 key" continuously which should bring up the "Windows Advanced Options Menu" as shown below. Use your arrow keys to move to "Safe Mode" and press Enter key.

NOTE: Login as the same user you were previously logged in with in the normal Windows mode.
2. When Windows loads, open up Windows Registry Editor.
To do so, please go to Start, type "registry" in the search box, right click the Registry Editor and choose Run as Administrator. If you are using Windows XP/2000, go to Start → Run... Type "regedit" and hit enter.
3. In the Registry Editor, click the [+] button to expand the selection. Expand:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
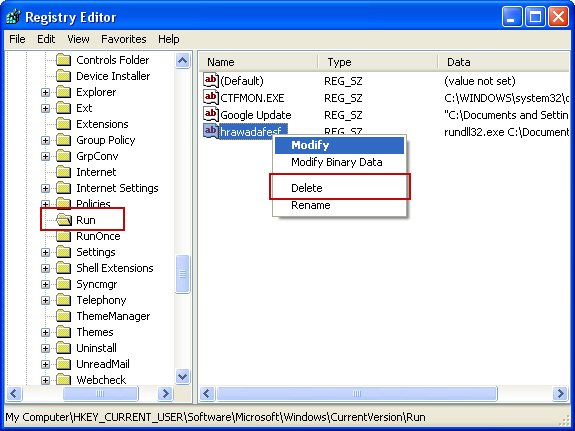
Look on the list to the right for an randomly named item. Write down the file location. Then right click the randomly named item and select Delete. Please note that in your case the file name might be different. Close Registry Editor.
In our case the malicious file (pg_0rt_0p.exe) was located in Application Data folder. So, we went there and simply deleted the file. We're running Windows XP.
File location: C:\Documents and Settings\Michael\Application Data\
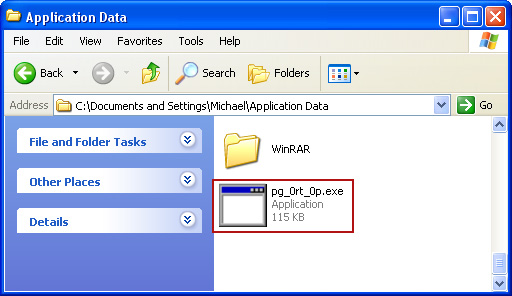
If you are using Windows Vista or Windows Seven, the file will be located in %AppData% folder.
File location: C:\Users\Michael\AppData\Romaming\
Finally, go into Windows Temp folder %Temp% and click Date Modified so the newest files are on top. You should see an exe file, possibly with the name pg_0rt_0p.exe (in our case it was exactly the same), but it may be different in your case. Delete the malicious file.
One more thing, check your Programs Startup list for the following entry:
[UserPATH]\Programs\Startup\ctfmon.lnk - C:\Windows\system32\rundll32.exe pointing to [UserPATH] \Temp\wpbt0.dll,FQ10 (or FQ11)
In our case it was ctfmon.lnk pointing to malicious file which then loads the fake ransom warning. Please note that in your case the file name might be different, not necessarily ctfmon.lnk. Simply disable or remove (if possible) such entry and restart your computer.
4. Restart your computer into "Normal Mode" and scan the system with legitimate anti-malware software.
5. Download recommended anti-malware software (direct download) and run a full system scan to remove the remnants of United States Courts virus.
To learn more about ransomware, please read Remove Trojan.Ransomware (Uninstall Guide).
















0 comments:
Post a Comment